Useful Resources Every IT Security Pro Should Know
Introduction
Experts in computer science, app dev, and cyber security, in conjunction with the general public, often provide valuable free resources to further the noble cause of creating a safer cyber world.
The following is a handy descriptive list of such projects, consisting of frameworks, feeds, blogs, exchanges, newsletters, alerts and advisories related to IT Security with a focus on threat and vulnerability intel.
The list contains vendor agnostic resources. Many major vendors offer advisories and bulletins specific to their products. Look for future posts on that topic.
Mitre Att&Ck®
MITRE is a not-for-profit corporation that provides a variety of services and R&D focused on improving national security. In their own words:
“MITRE was established to advance national security in new ways and serve the public interest as an independent adviser.”
An important free resource provided by the organization is the MITRE ATT&CK® Matrix. It offers insights on how and where to deploy effective controls - a concept referred to as the attack kill chain. It provides detailed attack descriptions with examples, as well as methods for mitigation and detection. Currently, it offers matrices for Enterprise, Mobile and IOC. An IT security pro should become acquainted with this framework to be successful in understanding common cyber attacks and their associated tactics, techniques and procedures (TTPs).
Watch for future posts containing a deeper analysis.

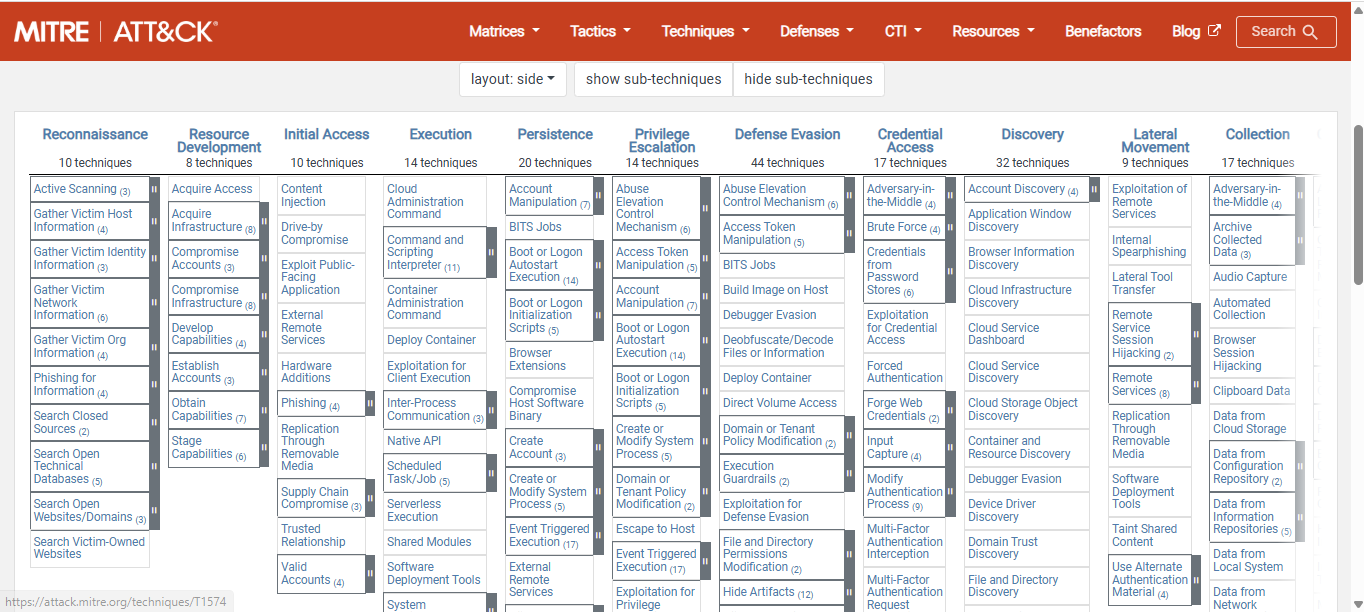
https://attack.mitre.org/
OWASP Top Ten
OWASP is a not-for-profit organization that focuses on software security through open source initiatives and community education. In their own words:
“The Open Worldwide Application Security Project (OWASP) is a nonprofit foundation that works to improve the security of software.”
A useful service provided by the organization is The OWASP Top Ten. Every four years, OWASP’s open community works to identify and describe the Top 10 most often exploited vulnerabilities in web applications. An IT security pro should be acquainted with this framework to understand how to successfully harden a web app against the most common flaws.
At the time of this post, OWASP is in the process of finalizing the latest version for 2025. The OWASP Top 10 from 2021 is the currently published list.
Stay tuned for future posts that will take a deeper dive.



https://owasp.org/www-project-top-ten/
LevelBlue - Open Threat Exchange (OTX)
LevelBlue and LevelBlue Labs are offshoots of AT&T in collaboration with WillJam Ventures offering a number of security services such as consulting, intel, and XDR. In their own words:
“Continuing the simplification of cybersecurity for organizations around the world, LevelBlue manages the risk so you can focus on what you do best.”
A short aside: AT&T acquired AlienVault and Alien Labs in 2018, and the OTX was previously named AlienVault OTX.
The OTX provides a massive catalogue of threat indicators or Indicators of Compromise (IoCs), curated from an array of publicly available sources and provided by subscribers. The list is constantly updated and populated with IOCs from known and emerging threats. It integrates seamlessly with the company’s SIEM/XDR platform LevelBlue USM Anywhere (Formerly AlienVault USM Anywhere), and can be leveraged by other security platforms through API, SDK and STIX/TAXII. The service also provides a sandbox for malware analysis of files and URLs, and a free agent for scanning endpoints. An IT security pro should be acquainted with this service and others of its kind to stay current with the latest trends and enhance the protection of their environments against known and validated identifiers.
Look for future posts on threat identification and hunting.




https://otx.alienvault.com/
https://levelblue.com/blogs/labs-research/
Internet Crime Complaint Center (IC3) Industry Alerts
A subsection of the FBI focused on cybercrime, the IC3 provides publicly available advisories about trending and active threats, as well as protection and remediation guidance. Crimes can also be reported through the service. In their own words:
“The mission of the Internet Crime Complaint Center is to provide the public and private sector with a mechanism to submit information to the Federal Bureau of Investigation concerning suspected cyber-facilitated criminal activity and to develop effective alliances with law enforcement and industry partners.”
The service is offered as downloadable reports containing background information and extensive technical detail. Email subscription is also available. In recent years, they developed an advisory specific to ransomware dubbed #StopRansomware. An IT security pro should be familiar with these reports and subscribe, so they can stay informed on the latest trends and be equipped with defense tactics.
Watch for future posts related to general mitigation strategies, and ransomware defense.


https://www.ic3.gov/CSA
CISA Cybersecurity Alerts & Advisories | Known Exploited Vulnerabilities Catalogue
CISA is a government agency focused on the coordination of critical infrastructure (CI) security. It provides guidance designed for CI, but also provides alerts and advisories free to the general public along with other cyber services. One of its most unique and valuable resources is the Known Exploited Vulnerabilities Catalogue (KEVC). In their own words:
“We lead the national effort to understand, manage, and reduce risk to our cyber and physical infrastructure.”
CISA can be followed on all the major social media platforms, and email subscription is available. Their reports are available online, and provide comprehensive detail on known and emerging threats and their mitigations. An IT security pro should be familiar with these reports to stay well-informed on the latest trends and be armed with defense tactics. An especially valuable resource, the KEVC, can be leveraged to improve threat, vulnerability and risk assessments by highlighting vulnerabilities that have been actively used for exploitation by malicious actors.
Look for future posts on threat identification and vulnerability management which will include tips on how to leverage the KEVC.







https://www.cisa.gov/news-events/cybersecurity-advisories
SANS Institute Internet Storm Center (ICS) | @RISK | NewsBites | OUCH!
SANS provides training and free resources on a large array of technologies. One of its most well-known offerings is the long running ICS. It provides news and insights into known and emerging threats free to the public. In their own words:
“Part of the SANS Technology Institute, the Internet Storm Center (ISC) stands as a beacon of vigilance and resilience in the ever-evolving landscape of cybersecurity.”
SANS can be followed on major social media platforms, and offers an API for devs. The ICS offers a well-maintained blog and a daily podcast. SANS also distributes three useful newsletters: an advisory called SANS @RISK, a semiweekly executive summary of news called SANS NewsBites, and a monthly security awareness newsletter called OUCH!. An IT security pro should follow these resources to stay well-informed on new and emerging threats, be armed with defense tactics and discover ideas for user awareness training.
Watch for future posts on useful news resources, and tips for user awareness training.









https://isc.sans.edu/
https://www.sans.org/newsletters/
Conclusion
The preceding resources are essential for any successful IT pro’s arsenal. Staying well-informed on the latest trends, and maintaining deep technical knowledge of existing threats, are vital to effective defense.
That was a long read. Time to relax.
Daily Cuppa
Today’s cup of tea is Organic Earl Grey provided by Equal Exchange.
Fair Trade, organic, and bursting with bergamot!
If you enjoyed this post or found use from it, feel free to buy the author a cup of tea.
